Scanning Tools
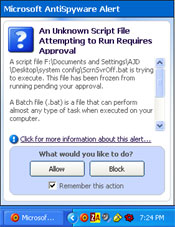
Microsoft’s AntiSpyware tool is a big leap forward in spyware prevention and removal. Though still in beta stage, this tool does a good job. For those of you not scared away by the beta tag it is sporting at the moment, it comes highly recommended, but is by no means perfect. Like any spyware removal utility, there are still things it misses. Its real-time protection system is much more user friendly than Spybot’s TeaTimer, albeit its huge nagging accept/deny pop-up dialog in the lower right hand corner of the screen can get annoying.
The two most common and most used spyware tools, Lavasoft’s Adaware and Spybot Search&Destroy have been cleaning infected systems for a few years now. Both still come highly recommended for your spyware combat arsenal.
However, an interesting factor has cropped up recenty where Lavasoft has removed a large well-known adware vendor called WhenU from their definitions database. That means any utilities produced by the WhenU vendor will be ignored by Adaware scans. This is a very disappointing move for Lavasoft to make. Pest Patrol and Aluria have also failed to include WhenU’s set of pests in their databases. Lavasoft’s response to its removal was that WhenU software was no longer a threat. Many spyware experts strongly disagree. There are other cases of known adware/spyware vendors going after the creators of spyware removal software, which can be found under this list of litigations pursued by spyware vendors when their software was included in various removal utilities.
As for Adaware, due to the raised voices against the failure to include WhenU in the Adaware removal definitions, Lavasoft released a separate removal tool, which does not do a great job at removing everything as displayed in this comparison between Adaware and Microsoft’s Anti-Spyware.
This just one large reason why a single scanning utility is not enough. Spyware utility companies should not be playing the “scratch-my-back-and-I’ll-scratch-yours” game with spyware vendors. In order to catch everything, you need to run multiple scanning utilities on your system. The Adaware/Spybot combination can do a good job at getting rid of adware/spyware, but it does not get rid of everything on your system, for spyware often changes faster than these companies can update their software. The spyware detection engines are starting to show their age by not picking up as much spyware as they used to in the past. In general, what one spyware utility misses, the other usually catches. Again, since Microsoft’s Anti-Spyware solution is new, it can combat many new strains of spyware, but be wary–it is still a beta, so check the items it detects and make sure they aren’t core Operating System modules or programs that you need or use (one such program called VNC for remote desktop control does get picked up, and yes, can be a security risk to an extent). Note that if you check for detected programs, it could also backfire because a program you have installed that you think may not have spyware, actually does. If you’re unsure, check this program search database.
In addition to the abovementioned spyware removal utilities, you may also want to check out X-Cleaner, and online spyware scanner, which is also available as a download. After running this utility following Spybot and Adaware, there were still a few items that were picked up that those utilities missed, which were mainly minor ad-related managers and BHO’s. Note that when the scan detects spyware during the scan process, a window similar to this should appear:
Make sure you uncheck the “Anonymously report this to detection server” option because this submission process takes a fair amount of time, as well as being form of data collection that is unnecessary for the end user for the most part. If you want to see SpywareGuide’s details on the detected item, click on the “Click for more information” link. It will list the item’s severity level (minor annoyance up to extremely dangerous), as well as basic information, the spyware category it falls into, and what problems/activities it is known to carry out.
Two other tools worthy of mention are Spy Sweeper and Pest Patrol. Both of these products are worthwhile, but are not free. There are plenty of free products available, therefore these tools are not necessary as a first line of defense. Spy Sweeper is a very good tool to use as a last resort option when other utilities were not successful in removing certain forms of spyware.
Spyware removal utilities do not usually pick up certain forms of malware, such as worms and Trojans, which usually come under the category of Anti-Virus protection. A good free AV application called AVG comes highly recommended and is often better than many AV packages you can purchase.
If you need an emergency scan quickly and don’t have an AV application installed, or AVG or some other utility isn’t picking anything up, but you still suspect a problem, using these online Trojan and virus scanners. Symantec’s AV Center Database contains information and removal tools for viruses, Trojans and worms, in case any of the abovementioned AV tools do not get rid of the virus/Trojan/worm.
Another good source for information on malware in general is 2-spyware.com, which has a database filled with malware-specific removal tools.
Last but not least, the final scanning utility you may want to run is HijackThis. HijackThis Is a technical scanning utility which lists all running processes and installed or altered system modules. It is best if this program is run right after startup.
Basic guides to using HijackThis and interpreting its findings can be found here and here. Additionally, this online tool will help interpret an HijackThis log by giving you a more detailed description of each entry and marking items as safe, unsafe, or unknown. This site was originally written in German, so don’t be surprised if some odd phrases or non-English words come up under the descriptions. In any case, it can still give you an idea of what the HijackThis entries may be. If you are still unsure about what may or may not be legitimate and what should be removed, many computer forums across the Internet that have experienced techs who are willing to assist users in identifying pests that appear in HijackThis logs. Simply copy and paste the log’s contents into a new thread and courteously request assistance. Also, be sure to clearly state what Operating System and Service Pack for that Operating System that you are running. PCMech’s Security & Privacy forum is one such place where you can find expert advice.



 AdamTheTech.com and respective content is Copyright 2003-2026.
AdamTheTech.com and respective content is Copyright 2003-2026.