What Kinds of Tactics Are Used?
Much of the time, spyware relies on persuading unaware or credulous users to download and install it by offering some kind of seemingly enticing bait, such as a prize, free money, a free service, or a free service that’s “better” and supposedly gives you a leg up on widely known legitimate software or services. 99% of the time, you can assume that it will not help in any way.
Here is a list of known spyware applications and a list of known spyware creators/vendors. Check these lists if you run across a program you want to install, but don’t really know anything about its origins or appear on unprofessional websites. If the software does not appear in the product search, it is either too new, too obscure, or not a threat.
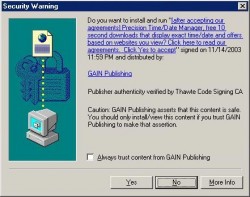
ActiveX
Accepting ActiveX plug-ins is an easy way to get spyware installed on your system. These are usually found on sites containing “underground” or “shady” content. Legitimate sites, such as Microsoft and Macromedia may ask to install installer engines if you are downloading updates or programs and usually say on the web page that you will be prompted to install an ActiveX plug-in. In cases like these, it is fine to let the ActiveX plug-in be installed, for it is needed to complete an operation. There is a big “however” to add to this-some sites with spyware are clever enough to include a notice for the ActiveX pop-up, so be careful. Pop-ups offering “free” something-or-other or “browser enhancements” should be avoided. Additionally, random junk that pops up on random sites where you are not explicitly downloading something should not be allowed to be installed.
Here is one such example of an ActiveX pop-up that should not be allowed to run:
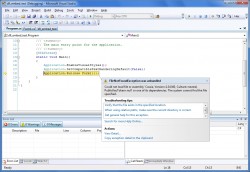
Fake Removal Tools
Beware of programs masquerading as adware or spyware removal tools, becoming known as “BetrayWare”. There are a small number of legitimate adware and spyware programs available; make sure that the removal tool program you download is a legitimate one. Other fake removal tools don’t go to cause harm to your system-some tools merely do nothing to combat the spyware problems, contrary to promises in their advertisements. Still others are simply clones of legitimate removal tools, but aren’t quite as good as the originals, where the core engine was swiped or licensed from, meaning that the major change is just a different GUI.
A comprehensive list of fake removal tools is available if you should want to check up on some removal tool that is being advertised or has been installed on your machine.
Misleading or Enticing Advertisements
Advertisers will use every trick in the book to grab your attention. They will use interactivity and movement, your sense of curiosity, your sense of humor, your sense of justice and right and wrong, your sense of greed and desire, and just plain unawareness or credulity simply to get you to click. Your click on an ad registers “Ka-Ching!” for the advertiser, both in terms of monetary profits and the installation of spyware for the purpose of data harvesting.
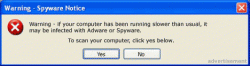
Users are often tricked by advertisements such as these:
At first glance, it looks like a serious Windows error message, and some users will click the “yes” almost automatically. However, if you look in the bottom right corner of the ad, it says “advertisement” in small light gray letters. It’s somewhat hard to catch if you are just skimming a webpage quick. The other thing to know about these ads is that it doesn’t matter where you click on the ad; the whole ad is a clickable image that can redirect the user to a spyware infested webpage, or to a page that offers a spyware infested scanning utility (BetrayWare).
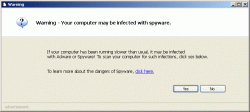
Another similar (and newer) advertisement is usually presented as a pop-up, and contains similar content as the previous example. See if you can spot the “advertisement” label in this ad:
Another common gimmick spyware creators/ventors love to use are the interactive ads; the ads where the user had to click on something that’s moving around. All those “punch the monkey and win”, and “knock out the boxer and win” type ads are redirects to places users would not really want to go on their own accord, since they are chockfull of spyware. No, you never actually win anything, and if you enter your email address on their website you will get spammed.
Here’s an example of an interactive ad promising that free $20 for performing an action. Notice the asterisk at the end of the phrase. That implies there is fine print that is attached to the deal that is being offered in the ad.
![]() Here’s an example of an animated lottery ad that goes to entice users hooked on the game of chance; all forms of lotteries and gambling.
Here’s an example of an animated lottery ad that goes to entice users hooked on the game of chance; all forms of lotteries and gambling.
![]() When it comes down to it, any ad involving money, offering free anything, offering great benefits of drug enhancements, offering better abs, offering a better love life, or any other enticing item or service, beware! It is most likely a scam to install spyware and try to get you to submit your email address for the purpose of spam. To make use of an overused geek cliché, Admiral Ackbar says, “It’s a trap!”
When it comes down to it, any ad involving money, offering free anything, offering great benefits of drug enhancements, offering better abs, offering a better love life, or any other enticing item or service, beware! It is most likely a scam to install spyware and try to get you to submit your email address for the purpose of spam. To make use of an overused geek cliché, Admiral Ackbar says, “It’s a trap!”




 AdamTheTech.com and respective content is Copyright 2003-2025.
AdamTheTech.com and respective content is Copyright 2003-2025.