Phishing
Phishing is not a form of direct spyware, but it can still be a simple, yet very effect tool for gathering personal information, sometimes leading to identity theft. It can be very scary if someone is taken in by a phishing attempt. As with anything else, there are a few things to look out for so it can be avoided.
- Read critically for spelling for grammatical errors.
- Legitimate sites/organizations never ask for personal information over email.
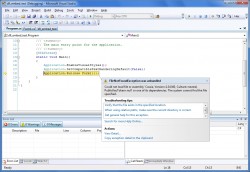
- Make sure the link included in a phishing attempt is not masked. Here is an example of what to look for:
- Notice that the text of the link displayed looks legitimate, whereas the real link address directs you to a phishing page. This of course screams “phishing attempt”.
- Check the webpage address for anything out of the ordinary. For instance, if the phishing attempt includes a link to a form that asks you to fill out personal information and does not contain the legitimate website’s base address, it is most likely a phishing attempt. For example, if the attempt happens to be for ebay and the link does not include ebay.com somewhere near the beginning of the address, it is most likely a phishing attempt. In addition to that, some phishing links can appear with letters switched around or omitted in the base address so it still looks like a legitimate address at a quick glance. www.microsoft.com may appear as www.mircosoft.com, www.micosoft, or may have an addition made to the front of the address such as www.msn-microsoft.com. It is also suggested that you do not actually click on the link because the website may be a host to all sorts of spyware and malware. So, if it doesn’t fool you into entering information, it will at least get that junk installed on your system.
- Beware of link addresses that contain an IP address. This is a big red flag that signifies that the server won’t be up long enough to be worth purchasing a domain name for it. In other words, it’s a host to a phishing site that probably won’t be online for too long. The IP address offers a direct link to the server without having to go through a domain name server, so no record of it would be logged. The link address can also be hidden by a mask, as shown in an earlier example.
- Beware of redirection links. Links that may look official may actually redirect you to a phishing webpage. For example, take a look at this eBay link: http://cgi4.ebay.com/ws/eBayISAPI.dll?MfcISAPICommand=RedirectToDomain&DomainUrl=http://www.pcmech.com Careful, now — It doesn’t really link to eBay, does it? (Update: Just before the time of publishing, this specific redirect exploit was addressed and fixed by ebay. For the record, it redirected to http://forum.pcmech.com, but any address could have been used.)
- Never fall into the trap of “get rich quick” schemes, especially if you are called to perform some sort of service beforehand, and especially if it’s for someone in a 3rd world country.
- Never fall into the trap of emails asking for money or to help shuffle money around, especially if they say something like, “Help me. I’m really a displaced prince and will have access to a numbered bank account I will share it if you help” or “Help, I was the victim of a horrible tragedy and could use your monetary assistance through this difficult time.” These are the kinds of scams where the phrase “a fool and their money are soon parted” can be applied today. Don’t fall into the trap!
- If you receive an email from a bank regarding account or personal information, or if it’s not from a bank you even use, it’s definitely a phishing attempt. Banks never ask for personal or account information by email. They usually contact by snail mail or phone. Also, it’s rare, but not unheard of phishing attempts (fraud) being carried out via snail mail or phone, although this method is usually more expensive than sending out emails, and isn’t used often for this reason.
- For any email asking for personal information regarding some sort of user or bank account, watch out for these (or similar) phrases found in the email’s subject or body: “Dear Valued Customer”, “Verify your account”, “If you don’t respond in [this amount of time], your account will be closed”, and “Click the link to gain access to your account”.
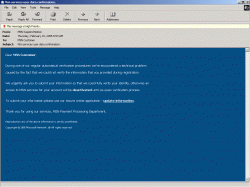
This MSN account phishing attempt is one of the most convincing phishing attempts that I have noted. At first glance, it looks quite legitimate and even sports a link to a page that looks convincingly legitimate. Take a look at it and see if you can apply some of the telltale signs of phishing.
Take a look at the spelling. It’s hard to catch at first glance, but “Automatical” is not a word. This anti-phishing site shows details of this specific phishing attempt. If you are ever not quite sure if something you receive is a phishing attempt, Google it. Search for a small phrase found in the phishing attempt and see you get any hits. If there are more than 3 hits that say “Yes, this is a phishing attempt,” it most likely is one. You can also take a look at these two anti-phishing sites for information on phishing attempts: http://www.antiphishing.org/ and http://www.millersmiles.co.uk/.



 AdamTheTech.com and respective content is Copyright 2003-2025.
AdamTheTech.com and respective content is Copyright 2003-2025.