IE AutoComplete Security Risk
IE’s AutoComplete feature enables users to begin typing website addresses, usernames, passwords, and passwords and have them automatically filled in if they have been entered before. This offers convenience and saves a little time while browsing. However, the downside is that it can be a security risk. Everything that was just mentioned can be accessed by someone using your computer, and sometimes by some forms of spyware. This will allow people to see what sites you have been visiting, gather personal information, and go as far as impersonate you to a degree.
To access the AutoComplete options, open up an IE window and go to Tools > Internet Options > “Content” tab > AutoComplete. Anything that has been checked will be remembered and saved.
IE Search Toolbars
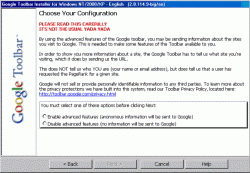
No matter what kind of search toolbar you install I guarantee it has some form of spyware in it. Yes, even the praised Google toolbar that acts as both a search bar and pop-up blocker. It is, however, one of the better pop-up blockers out there. Windows XP SP2’s pop-up blocker is defiantly way too restrictive even with the default settings, so even legitimate pop-up windows are blocked. Google toolbar seems to have a good balance. As for it containing spyware, take a look at this image from the installation procedure:
If you take a close look at the bottom where you have to make a selection to enable or disable something, you’ll notice that enable says, “Anonymous information will be sent to Google.” Translation: statistics on your browsing habits will be sent back to Google. This is a form of data collection. Make sure when you install Google toolbar that you hit “Disable”.
Most toolbars have some sort of spyware or adware bundled. There is yet to be a search bar that is totally free of spyware and adware. Suggestion: avoid them when possible, although there are a few reasonable exceptions, such as Google toolbar.
Install a Firewall
Basic firewalls have two uses. The first is to monitor connections and programs requesting access to the Internet, which is referred to an application firewall. This is a good way to see what programs are trying to access the Internet. It’s somewhat surprising to find that most applications actually ask for Internet access at one time or another. Application firewalls usually have 4 basic settings: allow this time, always allow, don’t allow this time, and never allow. These four options give the user the power to control which programs are allowed to access the Internet. It is also a good way to detect spyware that may be floating around on your system. Most often, they request Internet access at one time or another to “phone home”.
The second basic use of a firewall is to block certain forms of spyware and malware, protect from DoS attacks, block random, unrequested, or “background noise” traffic coming from the Internet, all of which can be accomplished for the most part by closing ports from outside intrusions.
In most cases, a single firewall can take care of both situations. Sygate Personal Firewall, Kerio Personal Firewall, or ZoneAlarm 4.5 would be adequate protection. Note, however, that there are compatibility issues with ZA 4.5 and XP SP2. More recent versions of ZA are available, but version 4.5 was the last good, bloat-free version, with version 5.5 being the last cost-free version. Windows XP SP2’s Internet Security is very good as well, however, it would not be wise to rely solely on this high profile target. First, it is far less customizable than other solutions and tends to be too restrictive, as to the traffic it is blocking. Second, when something is widely used, malicious software writers usually target the largest base of attack, namely, the Windows platform. The long short of it, use a firewall that doesn’t come with the Microsoft tag. It would also be wise to avoid Norton Security products. Newer versions (2002 and above) have been known to cause an array of random issues with Windows XP. Also avoid “System Utility”, or all-in-one packages. They may appear to help, but more often than not, they actually end up causing headaches and have a huge negative impact on your system by eating up system resources. All of the extra and unnecessary “stuff” that is added to the software package is really a bloated set of applications that can be replaced, most of the time, with either freeware or shareware applications that have smaller footprints (meaning, they are not resource hogs).
In any case, if you don’t have a firewall installed, your computer is completely open to attack. In less than 20 minutes, your computer will be full of all sorts of junk, and your security and privacy will be compromised. A firewall is one of the best pieces of software you could install on your system as a preventative measure to spyware and malware infestations.



 AdamTheTech.com and respective content is Copyright 2003-2024.
AdamTheTech.com and respective content is Copyright 2003-2024.